Learn why leading HR professionals trust ekincare! Explore Now

In the wake of this global pandemic, cybercriminals are among the first to sow discord, spread disinformation, and seek financial gain. In February 2020, the World Health Organization (WHO) released an advisory warning of ongoing scams amidst the outbreak of COVID-19.

As many companies adopt work-from-home policies in response to the COVID-19 pandemic, cybersecurity is a growing issue. While COVID-19 itself presents a significant global security risk to individuals and organizations across the world, cybercriminal activity around this global pandemic can result in financial damage and promote dangerous guidance, ultimately putting additional strain on efforts to contain the virus.
The “Live Coronavirus Data Map” from the John Hopkins Center for Systems Science and Engineering (CSSE) has been used as a lure to spread malware.
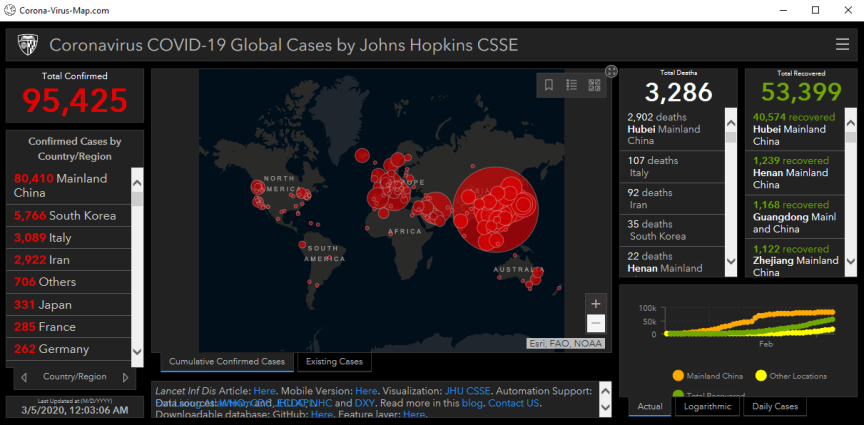
This interactive dashboard is being used by malicious websites (and possibly spam emails) to spread password-stealing malware.
According to Krebsonsecurity.com, a member of “several Russian language cybercrime forums began selling a digital coronavirus infection kit that uses the Hopkins interactive map as part of a Java-based malware deployment scheme. The kit costs $200 if the buyer already has a Java code signing certificate and $700 if the buyer wishes to just use the seller’s certificate.”
The lure is very realistic. It acts as a fully working online map of coronavirus infected areas, which is “resizable, interactive, and has real-time data from the World Health Organisation and other sources”. The offer selling the kit stated that “users will think that PreLoader is actually a map, so they will open it, spread it to their friends and it then goes viral!”.
Recently, links were sent to some Android phones (typically, via SMS or watering hole websites), promising an app tracking coronavirus which was again a lure.
Once the application is downloaded, people suspected to be operating from Libya can watch through the user’s smartphone camera, gain access to text messages or listen through the microphone.
Another Android app has also been detected by DomainTools, using the same map as a lure, but this time causing the phone to lock and asking for a ransomware payment for it to be unlocked. This ransomware is called CovidLock.
All of those malicious links or apps are a risk to healthcare organizations, as doctors or caregivers might innocently download these apps onto their smartphones or personal computers, and then connect them to their networks.
Even by accident, many employees are often the root cause of successful cyberattacks, according to Accenture’s 2018 State of Cyber Resilience survey. Data leakage (mobile users giving permissions to apps on their phones without checking security) potentially allows sensitive data to be forwarded. According to AccountancyAge, this “is due to smartphone users being more likely to check their emails frequently and being more likely to make a mistake by clicking a dodgy email link”.
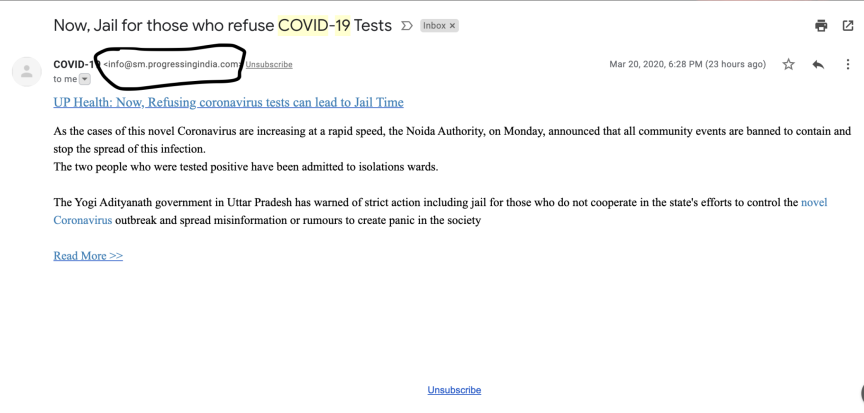
The above image depicts one such phishing email which can steal user's password or inject malware into their system.
Amidst this lockdown, when hackers are attempting to exploit this situation to monetize their efforts and even the cyberteam might get delayed to provide us with any help, it’s our utmost responsibility to be careful and read the sender email address before opening any link in the email.
While employees are an organization’s first line of defense, companies should encourage their employees to be skeptical of email from unfamiliar sources and coach them to take these precautions:
In this critical time, business leaders have a heightened responsibility to set clear expectations about how their organizations are managing security risks in the new work environments, leveraging new policies and technologies and empowering their employees. It’s important that messages on security come from the very top of an organization, and that good examples are set from the start.
Here are a few recommendations:
Taking these relatively straightforward steps at both an enterprise and individual level should help address some of the most common security risks facing our home-working environments. We should also recognize that our threat environment is not static, which means it's important to keep a close eye on evolving threats to avoid unnecessary additional costs and disruptions in a time when we can least afford them.